One Hit Hack Crossfire
One Hit Hack Crossfire' title='One Hit Hack Crossfire' />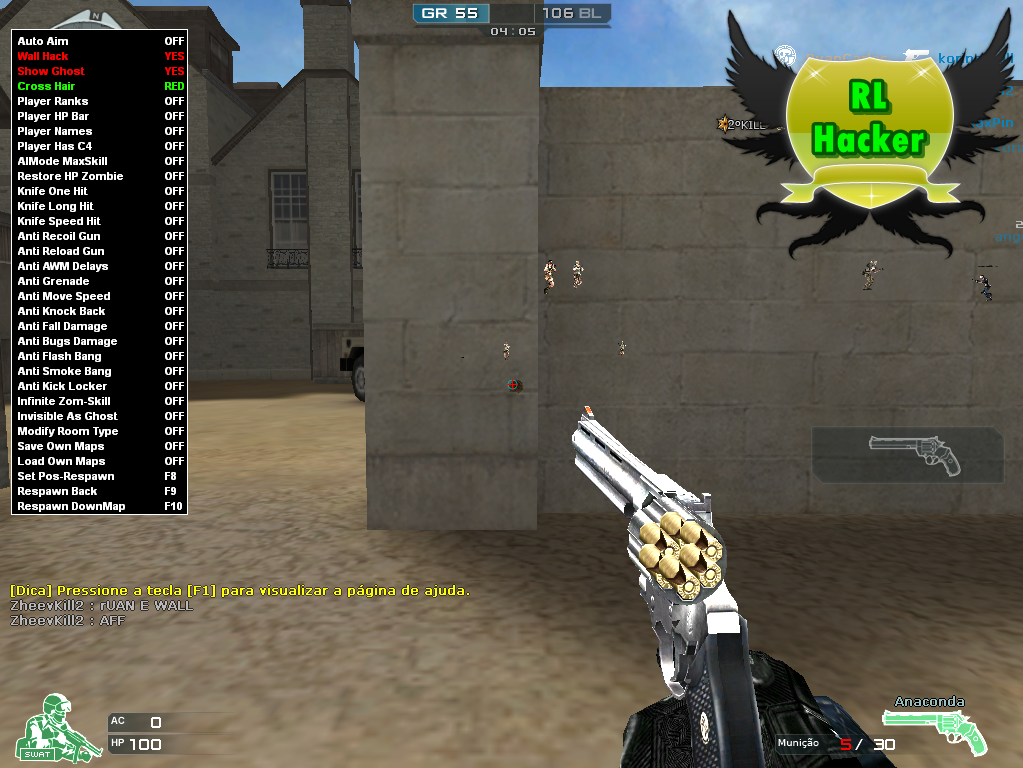 Hit The Troll Walkthrough video. Hit The Troll Video Walkthrough. Game Digimon Rumble Arena Pc. 29 Card Game For Windows Xp here. Back to Game.
Hit The Troll Walkthrough video. Hit The Troll Video Walkthrough. Game Digimon Rumble Arena Pc. 29 Card Game For Windows Xp here. Back to Game.  American demand for the Jaguar XK120 in particular spiked in 1950 after Phil Hill won first place in one at a race in Pebble Beach, California. Jewelry Store. The Payday gang have hit this one a number of times. Washington is full of stores like this. They can be easily entered at the front and back, and are. Parliament cyber attack Data breach under investigation after hackers target MPs emails. A cyber attack targeting the Houses of Parliament has caused a data breach after email accounts including a select committees mailbox were compromised. Investigators found that under 0. A spokesperson for the Houses of Parliament said officials representing both the Commons and Lords notified the Information Commissioners Office of a data breach in the wake of the attack. In the case of one compromised mailbox, for an unidentified House of Commons select committee, 7. A total of 3. 9 accounts operated by 2. MPs, a member of the House of Lords, administrative staff and a sub contractor, were hit by the attack. These compromises were made possible by the use of passwords that were compliant with the technical controls in place but did not conform to guidance issued by the Parliamentary Digital Service, a spokesperson said. Three of the six MPs had accounts compromised because their mailboxes were linked to their members of staff whose passwords were compromised. We have invested heavily in cyber security measures and will continue to do so. Emails hit as Parliament targeted by cyber security attackA series of technology changes including multi factor authentication have already been made to increase security. An email sent to everyone using a parliamentary address on 2. June said unusual activity and evidence of an attempted cyber attack had been discovered. Closer investigation by our team confirmed that hackers were carrying out a sustained and determined attack on all parliamentary user accounts in attempt to identify weak passwords, it continued. These attempts specifically were trying to gain access to users emails. The National Crime Agency and National Cyber Security Centre NCSC are investigating who was responsible, with initial suspicion turning to Russia and North Korea. Analysts said the hacking attempt used brute force tactics and could have been mounted by either state sponsored actors or criminal gangs to steal valuable information. Oz Alashe, a former special forces Lieutenant Colonel and chief executive officer of cyber security platform Cyb. Safe, said email accounts were a rich source of information for hackers He told The Independent criminal hackers harvest information including passwords, addresses and credit card numbers before selling them online, where they can be picked up and used by other actors, including foreign states. Many people use the same passwords for different accounts its not unusual, he added. A programmer works on decrypting source code in Taipei, Taiwan EPAThats why so many attackers are after these things once they compromise one account they can sell the password to be used to access others. The attempt came days after reports that Russian hackers had put passwords belonging to thousands of MPs, parliamentary staff, police employees and Foreign Office officials up for sale online. The information was believed to have been stolen from Linked. In, My. Space and other smaller sites, with many passwords easy to guess, incorporating memorable numbers and relatives names. Chris Pogue, a member of the US Secret Service Electronic Crimes Task Force, said hackers used machines that can guess 1. He equated the method of attack used on Parliament to shooting fish in a barrel amid a lack of awareness over secure passwords and the failure to separate systems handling sensitive and non sensitive information. Mr Pogue, the head of services, security, and partner integration at Australian technology firm Nuix, told The Independent Victims tend to overstate complexity and understate impact. A brute force attack doesnt mean Im going to make guesses as a human being, one after the other. What they do is build massive password databases based on every single dictionary word, cognate and misspelling. They can blow through your dogs name from when you were four years old in about 3. Fears of a cyber attack on Parliament had increased following the successful hacks targeting emails related to Hillary Clinton and Emmanuel Macrons presidential campaigns. The UK was also rocked by the Wanna. Cry ransomware attack that hit computers running outdated versions of Microsoft Windows around the world last month. Infecting more than 2. NHS as computers were left displaying only a page demanding bitcoin payments to decrypt files. It was followed by a second global ransomware attack using software known as Petya, as well as targeted assaults on American and Irish energy companies. A report on vulnerabilities in British defence released by the Royal United Services Institute RUSI earlier this month warned of the growing threat of cyber attacks. Enemies could take out military and civilian communication satellites and navigation systems, the report said, or target the UKs economy and crucial IT infrastructure causing chaos and panic. In any major future conflict, an important part of the battle will be threats to the UKs critical national infrastructure from hostile cyber operations, RUSIs report concluded. The cyber threat spectrum is not only relevant to defence but to government as a whole, especially to critical national infrastructure and the broader economy. Vladimir Putin has denied supporting hackers to launch cyber attacks on enemy states including Ukraine, or interfere in elections in the US, France and elsewhere. Silkroad Private Server Bot. Last month he conceded that patriotically minded hackers may have meddled in the American presidential election but added Were not doing this on the state level.
American demand for the Jaguar XK120 in particular spiked in 1950 after Phil Hill won first place in one at a race in Pebble Beach, California. Jewelry Store. The Payday gang have hit this one a number of times. Washington is full of stores like this. They can be easily entered at the front and back, and are. Parliament cyber attack Data breach under investigation after hackers target MPs emails. A cyber attack targeting the Houses of Parliament has caused a data breach after email accounts including a select committees mailbox were compromised. Investigators found that under 0. A spokesperson for the Houses of Parliament said officials representing both the Commons and Lords notified the Information Commissioners Office of a data breach in the wake of the attack. In the case of one compromised mailbox, for an unidentified House of Commons select committee, 7. A total of 3. 9 accounts operated by 2. MPs, a member of the House of Lords, administrative staff and a sub contractor, were hit by the attack. These compromises were made possible by the use of passwords that were compliant with the technical controls in place but did not conform to guidance issued by the Parliamentary Digital Service, a spokesperson said. Three of the six MPs had accounts compromised because their mailboxes were linked to their members of staff whose passwords were compromised. We have invested heavily in cyber security measures and will continue to do so. Emails hit as Parliament targeted by cyber security attackA series of technology changes including multi factor authentication have already been made to increase security. An email sent to everyone using a parliamentary address on 2. June said unusual activity and evidence of an attempted cyber attack had been discovered. Closer investigation by our team confirmed that hackers were carrying out a sustained and determined attack on all parliamentary user accounts in attempt to identify weak passwords, it continued. These attempts specifically were trying to gain access to users emails. The National Crime Agency and National Cyber Security Centre NCSC are investigating who was responsible, with initial suspicion turning to Russia and North Korea. Analysts said the hacking attempt used brute force tactics and could have been mounted by either state sponsored actors or criminal gangs to steal valuable information. Oz Alashe, a former special forces Lieutenant Colonel and chief executive officer of cyber security platform Cyb. Safe, said email accounts were a rich source of information for hackers He told The Independent criminal hackers harvest information including passwords, addresses and credit card numbers before selling them online, where they can be picked up and used by other actors, including foreign states. Many people use the same passwords for different accounts its not unusual, he added. A programmer works on decrypting source code in Taipei, Taiwan EPAThats why so many attackers are after these things once they compromise one account they can sell the password to be used to access others. The attempt came days after reports that Russian hackers had put passwords belonging to thousands of MPs, parliamentary staff, police employees and Foreign Office officials up for sale online. The information was believed to have been stolen from Linked. In, My. Space and other smaller sites, with many passwords easy to guess, incorporating memorable numbers and relatives names. Chris Pogue, a member of the US Secret Service Electronic Crimes Task Force, said hackers used machines that can guess 1. He equated the method of attack used on Parliament to shooting fish in a barrel amid a lack of awareness over secure passwords and the failure to separate systems handling sensitive and non sensitive information. Mr Pogue, the head of services, security, and partner integration at Australian technology firm Nuix, told The Independent Victims tend to overstate complexity and understate impact. A brute force attack doesnt mean Im going to make guesses as a human being, one after the other. What they do is build massive password databases based on every single dictionary word, cognate and misspelling. They can blow through your dogs name from when you were four years old in about 3. Fears of a cyber attack on Parliament had increased following the successful hacks targeting emails related to Hillary Clinton and Emmanuel Macrons presidential campaigns. The UK was also rocked by the Wanna. Cry ransomware attack that hit computers running outdated versions of Microsoft Windows around the world last month. Infecting more than 2. NHS as computers were left displaying only a page demanding bitcoin payments to decrypt files. It was followed by a second global ransomware attack using software known as Petya, as well as targeted assaults on American and Irish energy companies. A report on vulnerabilities in British defence released by the Royal United Services Institute RUSI earlier this month warned of the growing threat of cyber attacks. Enemies could take out military and civilian communication satellites and navigation systems, the report said, or target the UKs economy and crucial IT infrastructure causing chaos and panic. In any major future conflict, an important part of the battle will be threats to the UKs critical national infrastructure from hostile cyber operations, RUSIs report concluded. The cyber threat spectrum is not only relevant to defence but to government as a whole, especially to critical national infrastructure and the broader economy. Vladimir Putin has denied supporting hackers to launch cyber attacks on enemy states including Ukraine, or interfere in elections in the US, France and elsewhere. Silkroad Private Server Bot. Last month he conceded that patriotically minded hackers may have meddled in the American presidential election but added Were not doing this on the state level.